Core2 for AWS is no longer entering bootloader mode
-
there are 3 devices, 2 of them are no longer working as no way to enter boot loading mode, re-flash firmware is rendered impossible.
attempted to uses ESP-IDF, and manually pull down GPIO0 and press RESET to enter boot loading mode, still does not work.
it is a bit disappointed for such devices and the reliability, about 2 years’ service life or less. either CP2104 failure or the ESP32 no response, no clue. Other development boards with CP2102, always working for more than 6 years, so we would conclude this extends, the problem persisted with those M5Stack Core2 for AWS. DTR / RTS auto reset signal looks pretty the same as before, but serial response nothing, esptool prompts for timeout. M5burner is just a fancy wrapper with esptool encapsulated, and of course, the same report of timeout and no burn.
here is simple procedure for the test and hosted open source code, https://github.com/xiaolaba/ESP32_AWS_IoT_EduKit_quick_test
-
further testing and uses this official wrapper,
https://m5stack.oss-cn-shenzhen.aliyuncs.com/EasyLoader/Windows/CORE/EasyLoader_Core2_for_AWS_Default.exethe same result, definitely the malfunction of the device, but why ?
(
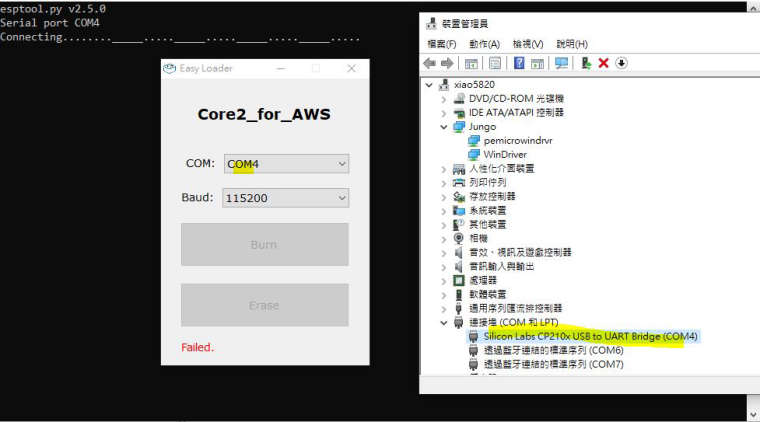 image url)
image url) -
@xiaolabam5 I want to mention in this forum that the easyloader .exe file in the previous comment (https://m5stack.oss-cn-shenzhen.aliyuncs.com/EasyLoader/Windows/CORE/EasyLoader_Core2_for_AWS_Default.exe) triggered a security alarm at my employer.
It has been listed as malware by Virustotal, and Crowdstrike, and I had to have my laptop processed by security after using it. It contains a trojan.
Here is the Virustotal hash for that file:
I am a little alarmed that an official M5stack file/tool is officially considered malware :(
We will see after IT/Security completes their deeper scans of my laptop, how much trouble I am in.
But on the other hand, my new M5stack AWS device looks very cool.
-
They found no damage from the file. Im thinking it must be a false positive? Anyone else ever have anti-malware or anti-virus trigger on m5stack stuff?
-
@mtylerjr if the software comes from China, it often triggers a malware due to the way the drivers are made and the fact that the OS only want you to use hardware that is approved to work with their own built in drivers.
-
@ajb2k3 Well, this had nothing to do with the OS this time. But yeah, Ive had my own code, compiled as an EXE, promptly quarantined by the over-zealous anti-malware system. My employer takes security...very very seriously. To the point where software guys like myself get frustrated over things like this.
But still, it was unnerving to be contacted by our cybersecurity team on the other side of the planet, telling me I'd set off alarms from several thousands of kilometers away, just from playing with my new m5stack devices I'd received that day, and that I'd have to have my machine scrubbed.
But it looks like nothing has come of it, and was a false alarm. I'll just stick to using them at home instead of at work. I could never get M5burner to work through the layers of security anyway.
BTW, Ive succeeded in geting both UIFlow1 and UIFlow2 working on my Core2 AWS. I basically bought it to use with UIFlow1 until UIFlow2 is more complete. Now I can use all my "only supported by UIFlow1" bits, while UIFlow2 grows.